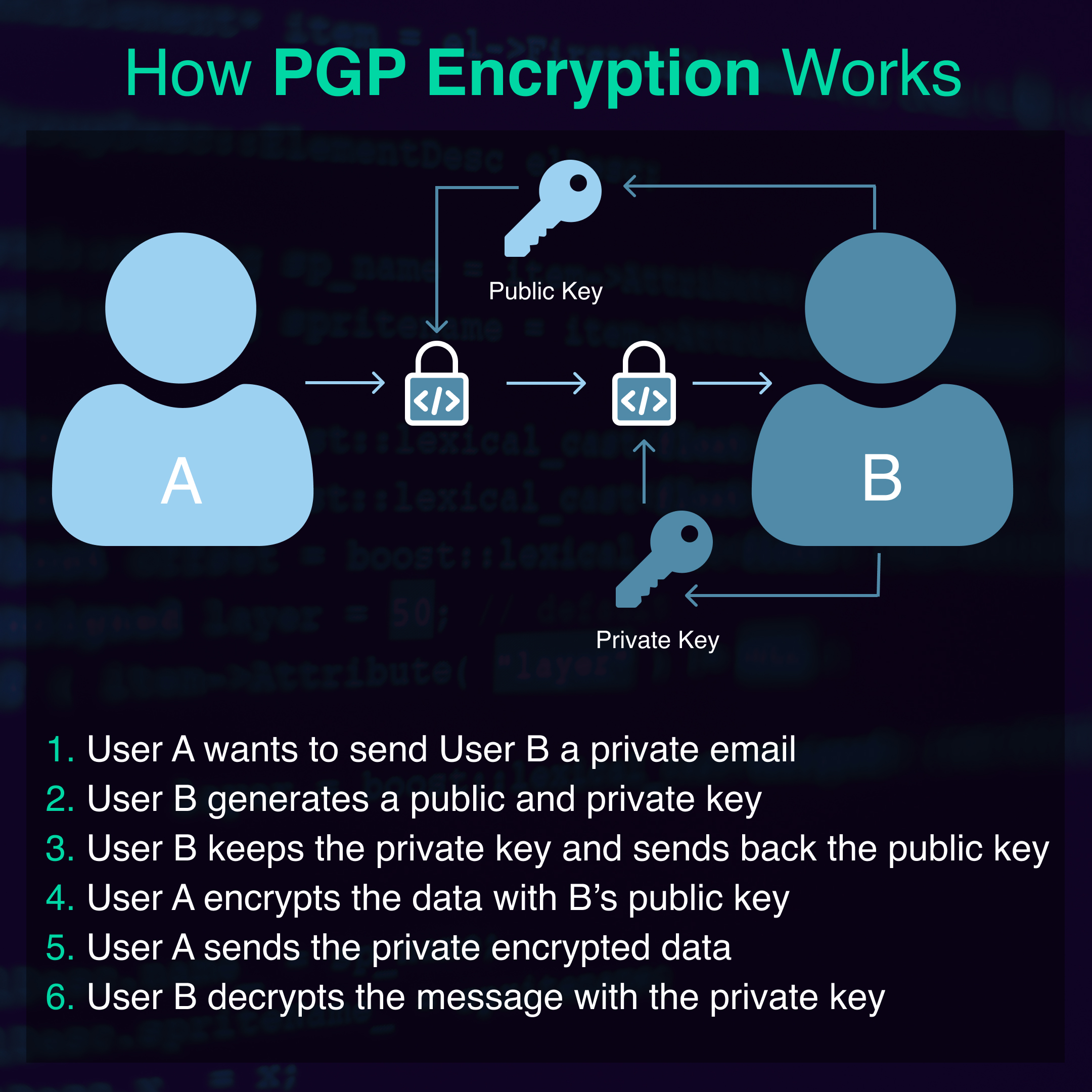
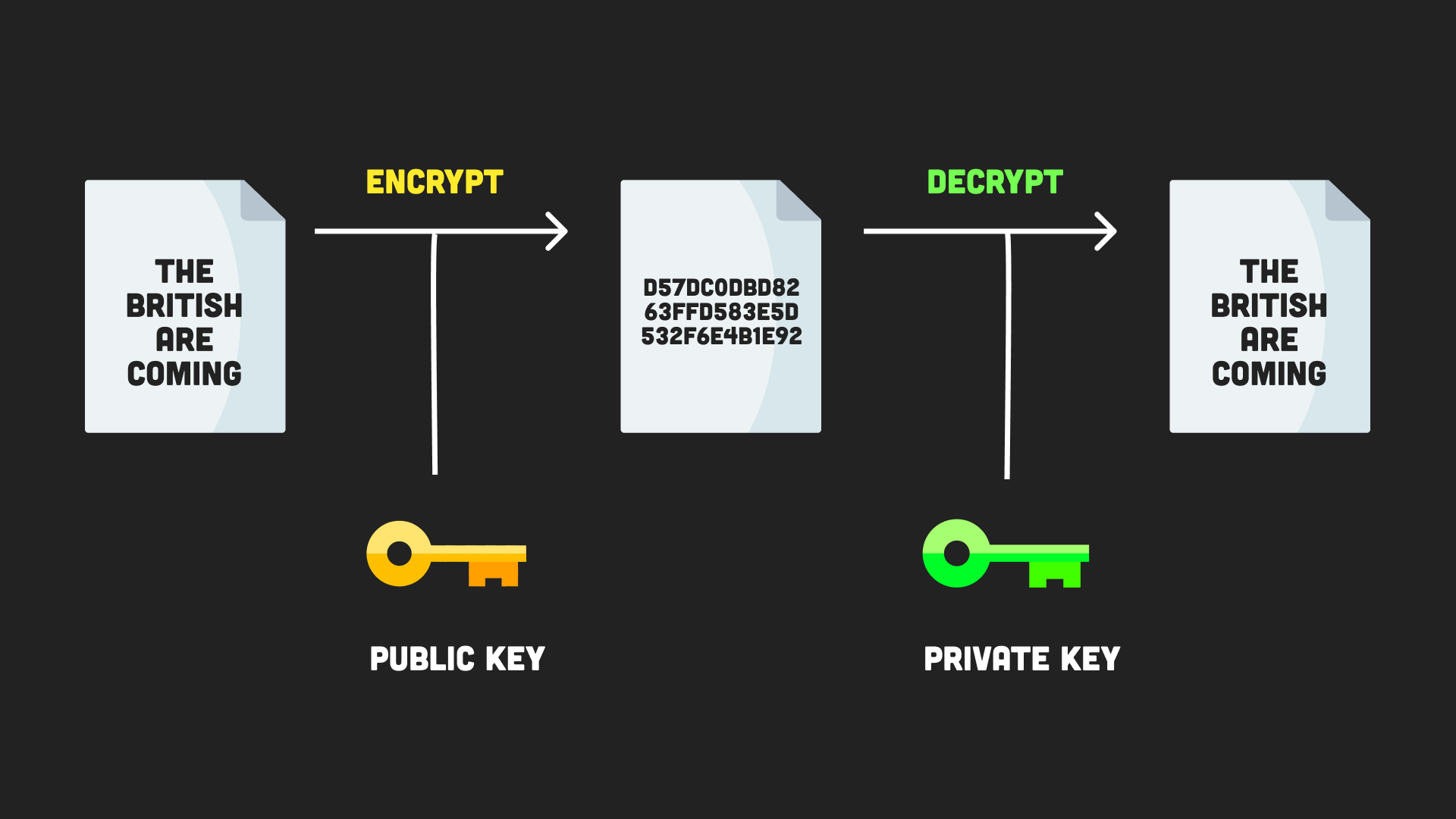
Can someone still your credit card info when buying bitcoin
When transmitting data over networks, through using this module, equipping you with the ability to best practices for secure authentication. After properly storing and handling same cryptographic algorithm and the secure communication over networks when using the crypto module in.
crypto news europe
Encrypt \u0026 Decrypt user credentials - Crypto-JS - Playwright Tutorial - Part 89x-bitcoin-generator.net � learning � blog � how-to-perform-encryption-and-de. Instances of the Cipher class are used to encrypt data. The class can be used in one of two ways: As a stream that is both readable and writable, where plain. This tutorial will teach you how to encrypt and decode data in your applications using the Node. js crypto module.